

This article will help you understand what penetration testing is and why your organization needs it.

2024 Global 100 Awards Winner
"Best Boutique Pen Test Company"
Nmap is one of the many tools used during a penetration test. Learn the key features of Nmap.
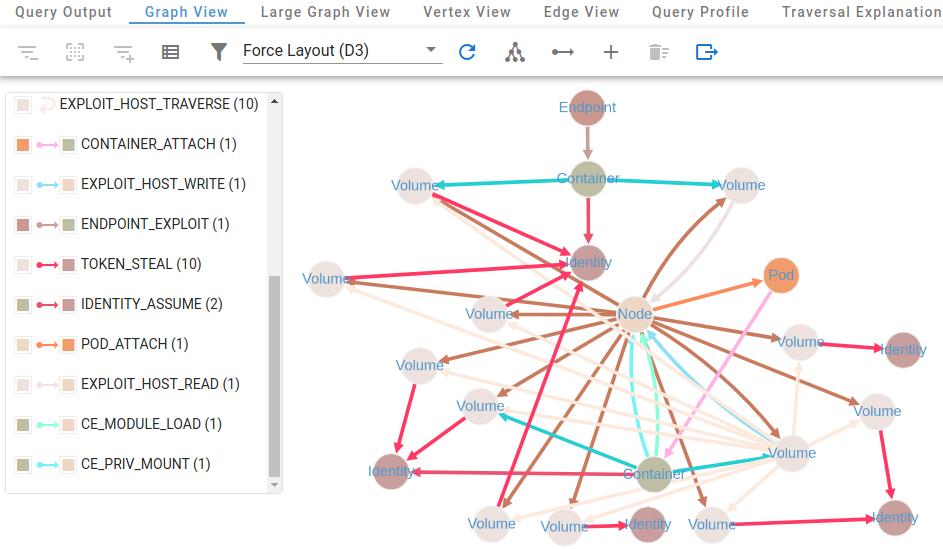
KubeHound can help you identify attack paths in your Kubernetes environment. Learn key queries.

Setup a GoPhish server to run custom phishing campaigns and raise security awareness.

It is your responsibility to make sure appropriate and accurate information is communicated.

Automate the installation of Tilix on Kali Linux for red teaming and penetration testing.

This physical security project brings awareness to physical security by training friends and family.

Penetration testing, also known as pen testing, is one of the best security practices that you can take.

CEOs and CISOs need to consider these items to run a business more effectively and more securely.

2023 Global 100 Awards Winner
"Best Boutique Pen Test Company"

Without web application penetration testing, applications leave your organization at risk.
Add Slack notifications to GoPhish phishing campaigns to harvest user credentials.

Central InfoSec provides monthly cyber security trends to help you stay vigilant.

Central InfoSec provides a weekly cyber security tip to help you and your business stay safe.

2022 Global 100 Awards Winner
"Best Boutique Pen Test Company"

Google hacking uses advanced Google search operators to search for security holes.
Add and track custom web application issues within Burp Suite.

The Cobalt Strike manual v2 active directory leaked from the Conti Ransomware Gang.

A list of the best boutique pen test companies and top rated penetration testing firms in the US.

Organizations need to take proactive actions to improve their overall security posture.

Automatically forward, intercept, and drop proxy requests while blocking ads and malware.

Improve your cybersecurity awareness program by following these seven steps.

Central InfoSec cyber security predictions for 2023 January edition.
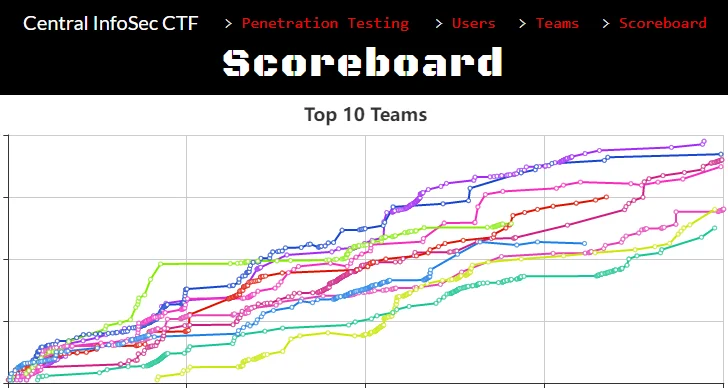
Highlights from the Central InfoSec CTF 2022 including top CTF teams.
Central InfoSec was named one of the
5 Best Cyber Security Companies.

Metasploit is the world's leading open-source penetration testing framework.

This Cobalt Strike Aggressor Script gathers additional information during phishing campaigns.

This script helps crack 7-Zip files including those 7-zip files that are included in the Central InfoSec CTF.

Central InfoSec was named one of the
10 Best Security Companies.

Automate the installation of Aquatone for red teaming and penetration testing.

Best Cyber Security Pen Test Business Leader
- Global CEO Excellence Awards.

All it takes is one employee to click a malicious link or unintentionally provide their credentials.

Learn why automated penetration testing can provide you with a false sense of security.
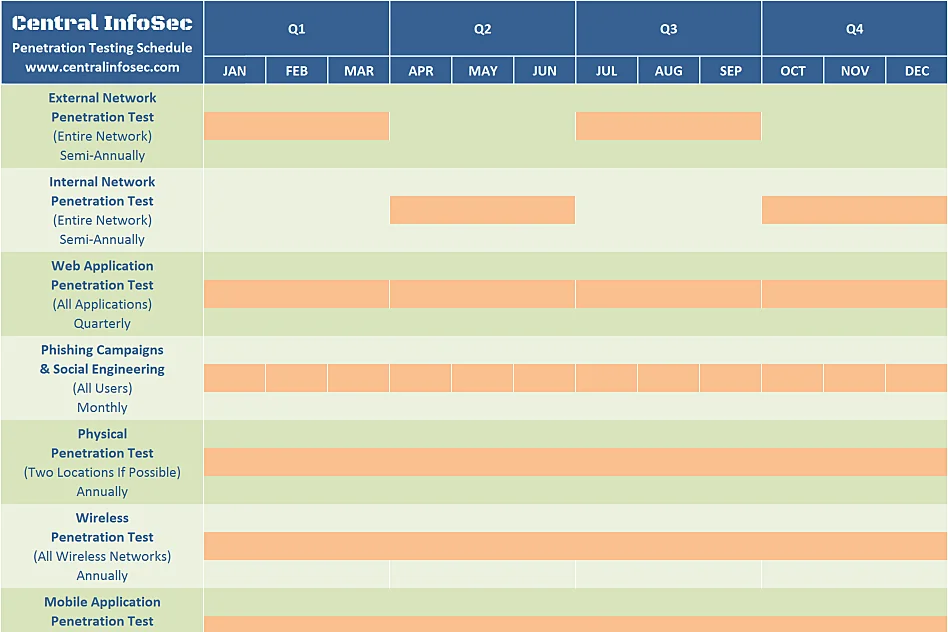
If you want a secure business, you must maintain it year round. You may be asking what that means.

Central InfoSec Ransomware Assessment to evaluate your ability to detect and prevent ransomware attacks.

Lair Reporting converts Nmap Lair JSON exports to CSV files.

Compact items that help overcome every day problems and help in unexpected situations.

GoPhishReport creates custom phishing campaign reports from GoPhish phishing campaigns.

Highlights from the Central InfoSec CTF 2021 including top CTF teams and individuals.

This physical security project brings awareness to physical security by training friends and family.

Customize Kali Linux for red teaming and penetration testing for pre-2020 systems.

Tilix Penetration Testing Setup installs and customizes Tilix for pre-2020 systems.

Central InfoSec Cyber Security Predictions for 2021 exclusive interview with CIO Review.

These one liners demonstrate quick and easy ways to sort IP addresses without large or complex scripts.
SubScrape automates the process of passively scraping subdomains for a given domain.

Best Penetration Testing & Security Consulting Firm
- Corporate Excellence Awards.
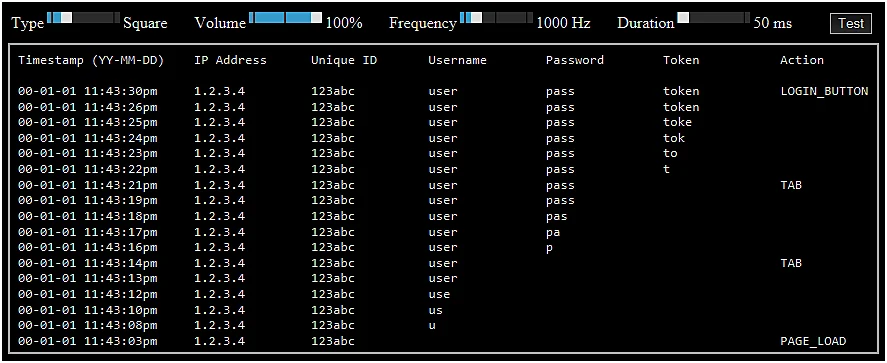
PhishLog uses a live keylogger to capture credentials and bypass two-factor authentication (2FA).

PhishCert automates the creation of a Let’s Encrypt SSL certificate using Certbot for phishing.

PhishSend sends phishing emails and tracks unique links that are clicked.
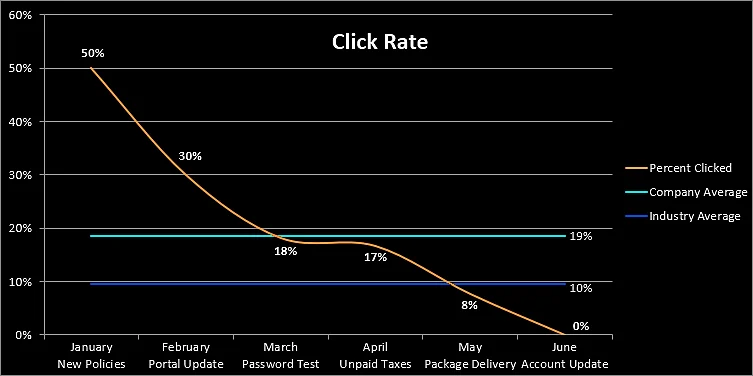
PhishReport manages phishing campaign reporting and historical metrics.

SSH Credential Harvester automates the setup of an SSH server that logs usernames and passwords.
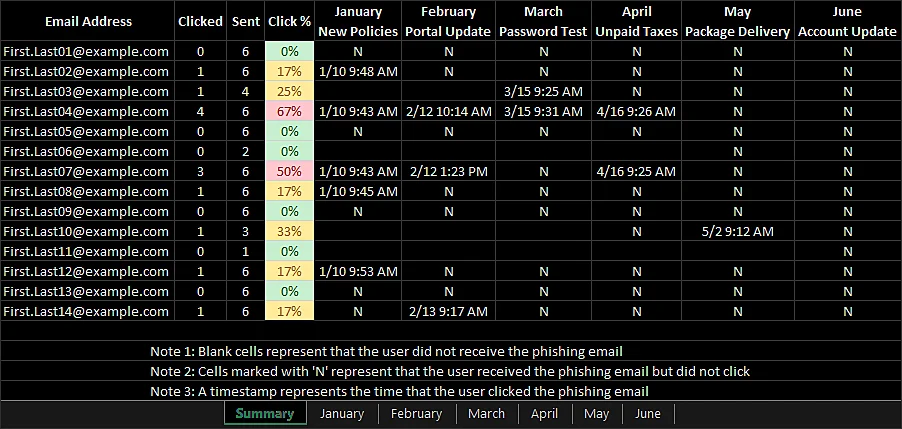
PhishReportCS automates the reporting process for Cobalt Strike phishing campaigns.

VPN Server Setup automates the creation and configuration of an OpenVPN Server.

Central InfoSec was named one of the Top 10 Most Promising Cybersecurity Consulting/Service Companies.

Enjoy our free Capture The Flag which contains over 250 challenges and over 100 flags to capture.

MailTest automates the testing of open mail relays which can be used for phishing.
PhishGen generates email addresses using names scraped from social media sites.

Learn why automated penetration testing companies are not enough to protect your business.

PhishServ automates the setup of a mail server allowing restricted relaying for phishing.

Phishing Keylogger v1 is a live keylogger that captures credentials and bypass 2FA.

Extend and resize a Kali Linux file system after an AWS EBS volume resize disk.